Unlock Fortinet Mastery: FCP - FortiAnalyzer 7.4 Analyst Exam Success Awaits
Which two methods can you use to send notifications when an event occurs that matches a configured event handler? (Choose two.)
Correct : B, C
In FortiAnalyzer, event handlers can be configured to trigger specific notifications when an event matches defined criteria. These notifications are designed to alert administrators in real time about critical events.
Option B - Send SNMP Trap:
FortiAnalyzer supports sending SNMP traps as one of the notification methods when an event matches an event handler. This allows integration with SNMP-enabled network management systems, which can then trigger further alerts or actions based on the trap received.
Conclusion: Correct.
Option C - Send SMS Notification:
FortiAnalyzer also supports SMS notifications, enabling alerts to be sent via SMS to predefined recipients. This method is useful for administrators who require immediate alerts but may not have access to email or other notification systems at all times.
Conclusion: Correct.
Option A - Send Alert through Fabric Connectors:
While Fabric Connectors allow FortiAnalyzer to interact with other parts of the Security Fabric, they are primarily used for data sharing and automation rather than directly for sending alerts or notifications.
Conclusion: Incorrect.
Option D - Send Alert through FortiSIEM MEA:
FortiSIEM integration allows for data sharing and further analysis within the Fortinet ecosystem, but it does not directly act as a notification method from FortiAnalyzer itself.
Conclusion: Incorrect.
Conclusion:
Correct Answe r : B. Send SNMP trap and C. Send SMS notification
These options represent valid notification methods for FortiAnalyzer's event handler configuration.
FortiAnalyzer 7.4.1 documentation on event handler configuration and available notification methods.
Start a Discussions
Exhibit.
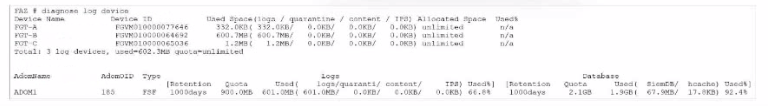
What can you conclude from this output?
Correct : C
The exhibit displays a diagnose log device output on a FortiAnalyzer, showing details about disk space usage and quotas for different FortiGate devices and ADOMs (Administrative Domains). Here's a breakdown of key details:
Disk Quota for Quarantined Files:
The output includes columns labeled for used space in categories such as 'logs,' 'quarantine,' 'content,' and 'DB.' For each device, the quarantine column consistently shows 0.0KB used, indicating that there is no disk quota allocated or utilized for quarantining files.
Conclusion: Correct.
FGT_B as Security Fabric Root:
There is no direct indication from this output that specifies FGT_B is the root of the Security Fabric. Information on Security Fabric topology or root designation would typically come from a Security Fabric configuration command rather than a disk usage summary.
Conclusion: Incorrect.
Allocated Disk Quota for ADOM1:
The output shows the quota for ADOM1 is 'unlimited,' not a fixed 3 GB quota. Therefore, there is no set 3 GB limit for ADOM1.
Conclusion: Incorrect.
Comparison of Archive Logs and Analytic Logs:
The output does not differentiate between archive logs and analytic logs; it only shows overall disk usage by type (e.g., logs, quarantine). Therefore, no conclusion can be made about which type of logs (archive or analytic) is using more space.
Conclusion: Incorrect.
Conclusion:
Correct Answe r : A. There is no disk quota allocated to quarantining files.
This answer aligns with the observed data, where no disk space is used or allocated for quarantine files.
FortiAnalyzer 7.4.1 documentation on diagnose log device command usage and disk quota settings.
Start a Discussions
Exhibit.
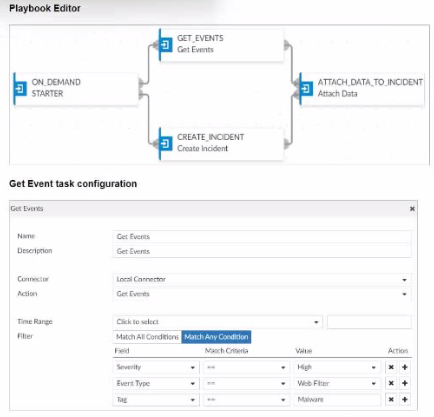
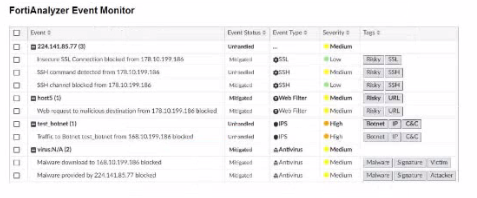
Assume these are all the events that exist on the FortiAnalyzer device.
How many events will be added to the incident created after running this playbook?
Correct : D
In the exhibit, we see a playbook in FortiAnalyzer designed to retrieve events based on specific criteria, create an incident, and attach relevant data to that incident. The 'Get Event' task configuration specifies filters to match any of the following conditions:
Severity = High
Event Type = Web Filter
Tag = Malware
Analysis of Events:
In the FortiAnalyzer Event Monitor list:
We need to identify events that meet any one of the specified conditions (since the filter is set to 'Match Any Condition').
Events Matching Criteria:
Severity = High:
There are two events with 'High' severity, both with the 'Event Type' IPS.
Event Type = Web Filter:
There are two events with the 'Event Type' Web Filter. One has a 'Medium' severity, and the other has a 'Low' severity.
Tag = Malware:
There are two events tagged with 'Malware,' both with the 'Event Type' Antivirus and 'Medium' severity.
After filtering based on these criteria, there are four distinct events:
Two from the 'Severity = High' filter.
One from the 'Event Type = Web Filter' filter.
One from the 'Tag = Malware' filter.
Conclusion:
Correct Answe r : D. Four events will be added.
This answer matches the conditions set in the playbook filter configuration and the events listed in the Event Monitor.
FortiAnalyzer 7.4.1 documentation on event filtering, playbook configuration, and incident management criteria.
Start a Discussions
Which statement about SQL SELECT queries is true?
Correct : D
Option A - Purging Log Entries:
A SELECT query in SQL is used to retrieve data from a database and does not have the capability to delete or purge log entries. Purging logs typically requires a DELETE or TRUNCATE command.
Conclusion: Incorrect.
Option B - WHERE Clause Requirement:
In SQL, a SELECT query does not require a WHERE clause. The WHERE clause is optional and is used only when filtering results. A SELECT query can be executed without it, meaning this statement is false.
Conclusion: Incorrect.
Option C - Displaying Database Schema:
A SELECT query retrieves data from specified tables, but it is not used to display the structure or schema of the database. Commands like DESCRIBE, SHOW TABLES, or SHOW COLUMNS are typically used to view schema information.
Conclusion: Incorrect.
Option D - Usage in Macros:
FortiAnalyzer and similar systems often use macros for automated functions or specific query-based tasks. SELECT queries are typically not included in macros because macros focus on procedural or repetitive actions, rather than simple data retrieval.
Conclusion: Correct.
Conclusion:
Correct Answe r : D. They are not used in macros.
This aligns with typical SQL usage and the specific functionalities of FortiAnalyzer.
FortiAnalyzer 7.4.1 documentation on SQL queries, database operations, and macro usage.
Start a Discussions
Exhibit.
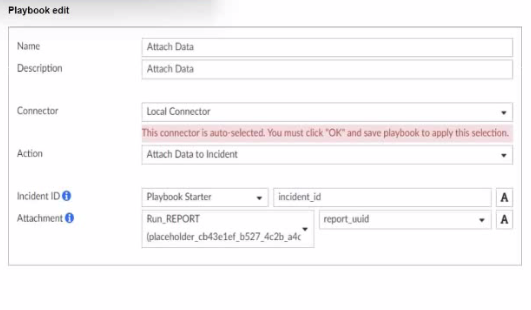
What is the analyst trying to create?
Correct : B
In the exhibit, the playbook configuration shows the analyst working with the 'Attach Data' action within a playbook. Here's a breakdown of key aspects:
Incident ID: This field is linked to the 'Playbook Starter,' which indicates that the playbook will attach data to an existing incident.
Attachment: The analyst is configuring an attachment by selecting Run_REPORT with a placeholder ID for report_uuid. This suggests that the report's UUID will dynamically populate as part of the playbook execution.
Analysis of Options:
Option A - Creating a Trigger Variable:
A trigger variable would typically be set up in the playbook starter or initiation configuration, not within the 'Attach Data' action. The setup here does not indicate a trigger, as it's focusing on data attachment.
Conclusion: Incorrect.
Option B - Creating an Output Variable:
The field Attachment with a report_uuid placeholder suggests that the analyst is defining an output variable that will store the report data or ID, allowing it to be attached to the incident. This variable can then be referenced or passed within the playbook for further actions or reporting.
Conclusion: Correct.
Option C - Creating a Report in the Playbook:
While Run_REPORT is selected, it appears to be an attachment action rather than a report generation task. The purpose here is to attach an existing or dynamically generated report to an incident, not to create the report itself.
Conclusion: Incorrect.
Option D - Creating a SOC Report:
Similarly, this configuration is focused on attaching data, not specifically generating a SOC report. SOC reports are generally predefined and generated outside the playbook.
Conclusion: Incorrect.
Conclusion:
Correct Answe r : B. The analyst is trying to create an output variable to be used in the playbook.
The setup allows the playbook to dynamically assign the report_uuid as an output variable, which can then be used in further actions within the playbook.
FortiAnalyzer 7.4.1 documentation on playbook configurations, output variables, and data attachment functionalities.
Start a Discussions
Total 56 questions