Master Fortinet FCP - FortiWeb 7.4 Administrator: Ace Your FCP_FWB_AD-7.4 Exam!
Refer to the exhibit.
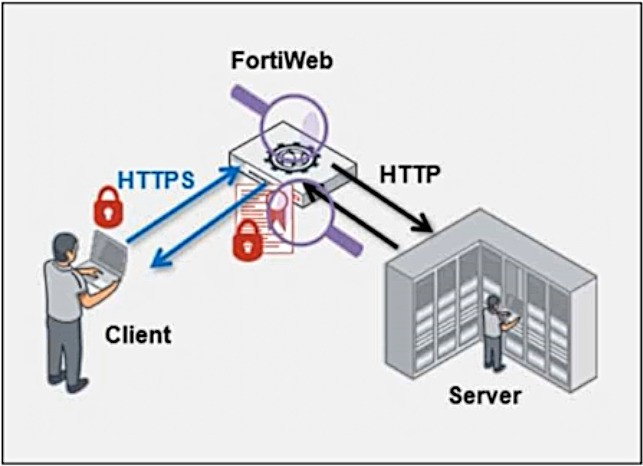
Which statement is true?
Correct : B
In the diagram, FortiWeb is positioned between the client and the server, handling encrypted HTTPS traffic from the client and sending unencrypted HTTP traffic to the server. This indicates that FortiWeb is performing SSL offloading, which means it is decrypting the HTTPS traffic from the client, inspecting it, and then re-encrypting the traffic before forwarding it to the server.
Start a Discussions
How are bot machine learning (ML) models different from API or anomaly detection models?
Correct : A
Bot ML models analyze multiple connections over time instead of analyzing each connection as a single unit: This is the key distinction. Bot ML models focus on analyzing patterns over a period of time, looking at behavioral patterns across multiple requests or connections from the same source to identify potential bot activity. Unlike traditional anomaly detection or API models that may focus on single connections or individual transactions, bot detection typically examines aggregated behavior to identify patterns indicative of bots, such as high-frequency requests or unusual traffic flows.
Start a Discussions
In which two operating modes can FortiWeb modify HTTP packets? (Choose two.)
Correct : B, D
Virtual proxy: In virtual proxy mode, FortiWeb acts as an intermediary between clients and the server, and it can modify HTTP packets. It performs various security checks, such as inspecting and filtering HTTP traffic before forwarding it to the web server.
Reverse proxy: In reverse proxy mode, FortiWeb sits between the client and the server, handling incoming requests from clients, modifying or inspecting HTTP packets as needed, and forwarding them to the backend servers.
Start a Discussions
Which three security features must you configure on FortiWeb to protect API connections? (Choose three.)
Correct : B, C, E
Machine learning (ML)-based API protection: ML-based API protection helps detect and mitigate abnormal behavior in API traffic, such as bot attacks or abuse, by learning and adapting to normal traffic patterns.
API schema validation: API schema validation ensures that the API requests conform to the defined schema (e.g., checking the structure, fields, and types in the API calls). This helps prevent attacks like XML or JSON injection by ensuring only valid requests are processed.
API user key enforcement: Enforcing API user key authentication requires clients to provide valid API keys, ensuring only authorized users can access the API. This is crucial for controlling access to the API.
Start a Discussions
Refer to the exhibit.
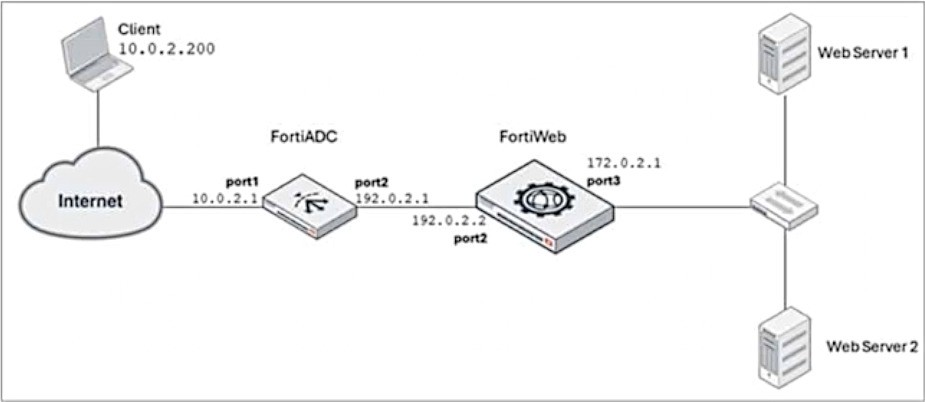
FortiADC is applying SNAT to all inbound traffic going to the servers.
When an attack occurs, FortiWeb blocks traffic based on the 192.0.2.1 source IP address, which belongs to FortiADC. This setup is breaking all connectivity and genuine clients are not able to access the servers.
What can the administrator do to avoid this problem? (Choose two.)
Correct : C, D
Place FortiWeb in front of FortiADC: This configuration change places FortiWeb between the client and FortiADC, so that FortiWeb can directly inspect and protect the incoming traffic before FortiADC applies SNAT (Source Network Address Translation). By placing FortiWeb in front, it will have access to the real client IP addresses, and it will be able to properly identify and handle attack traffic without blocking legitimate client traffic.
Enable and configure the Use X-Forwarded-For setting on FortiWeb: This setting allows FortiWeb to extract the original client IP address from the X-Forwarded-For header in the HTTP request, which is inserted by FortiADC when performing SNAT. With this setting enabled, FortiWeb will be able to block traffic based on the original client IP address rather than the SNATed IP address (192.0.2.1), preserving the accuracy of the security measures.
Start a Discussions
Total 36 questions