Unlock HP Aruba Certified Network Security Expert Written Exam HPE6-A84 Success
Ready to conquer the HP Aruba Certified Network Security Expert Written Exam HPE6-A84? Don't let anxiety hold you back. Our meticulously crafted practice questions are your secret weapon, available in PDF, web-based, and desktop formats to suit your study style. Imagine walking into the exam room with unshakeable confidence, knowing you've mastered cutting-edge network security concepts. As businesses scramble for cybersecurity talent, your certification could be the key to unlocking prestigious roles and lucrative opportunities. But hurry – the digital landscape evolves rapidly, and so do our materials. Join thousands of successful candidates who've trusted our expert-designed resources to navigate the complexities of Aruba technologies. Whether you're a seasoned pro or newcomer, we've got your back. Ready to transform your career? Your journey to network security expertise starts here.
You are configuring gateway IDS/IPS settings in Aruba Central.
For which reason would you set the Fail Strategy to Bypass?
Correct : A
Start a Discussions
How does Aruba Central handle security for site-to-site connections between AOS 10 gateways?
Correct : B
Start a Discussions
Refer to the exhibit.
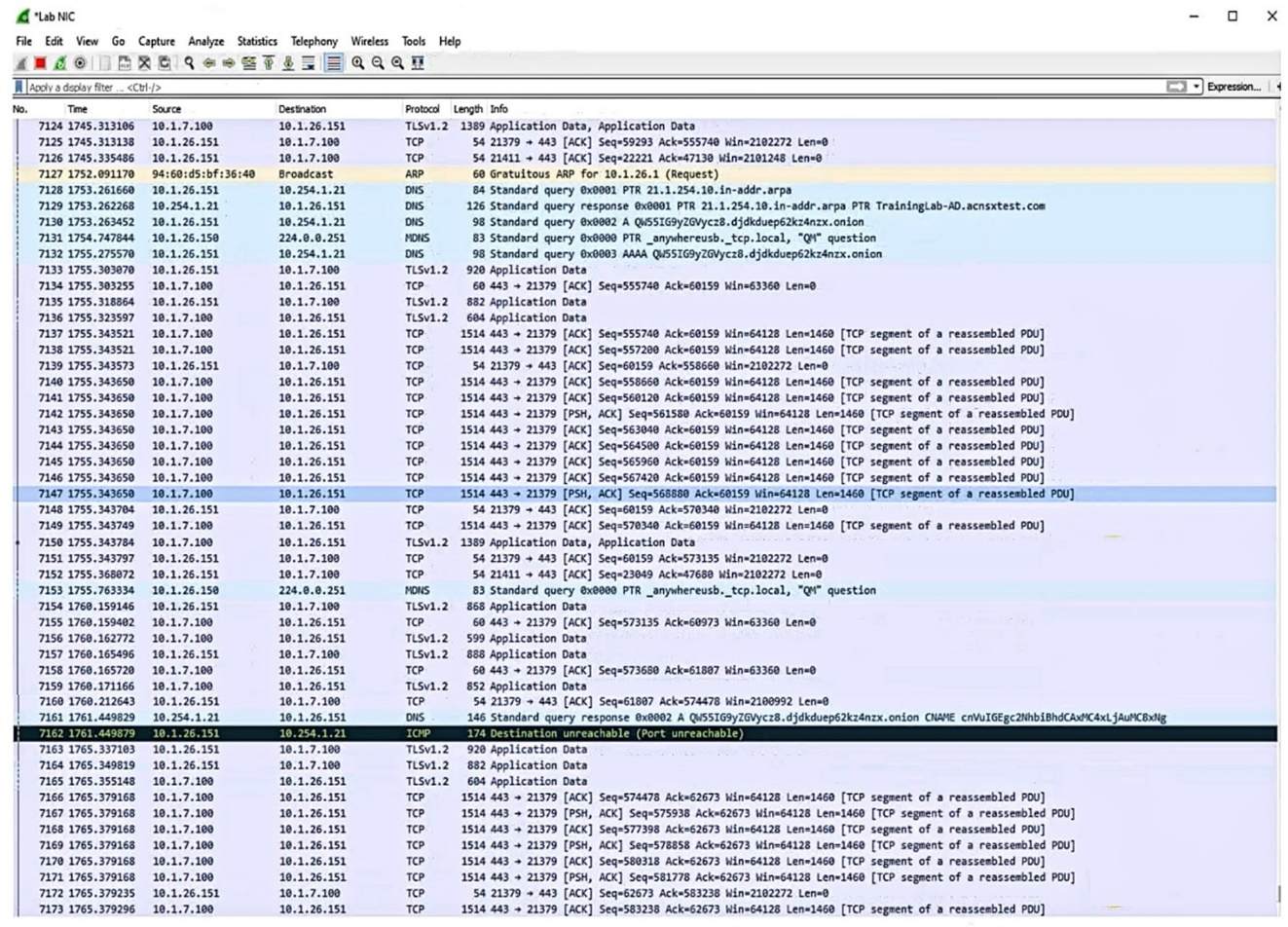
Which security issue is possibly indicated by this traffic capture?
Correct : C
Start a Discussions
You are working with a developer to design a custom NAE script for a customer. You are helping the developer find the correct REST API resource to monitor.
Refer to the exhibit below.
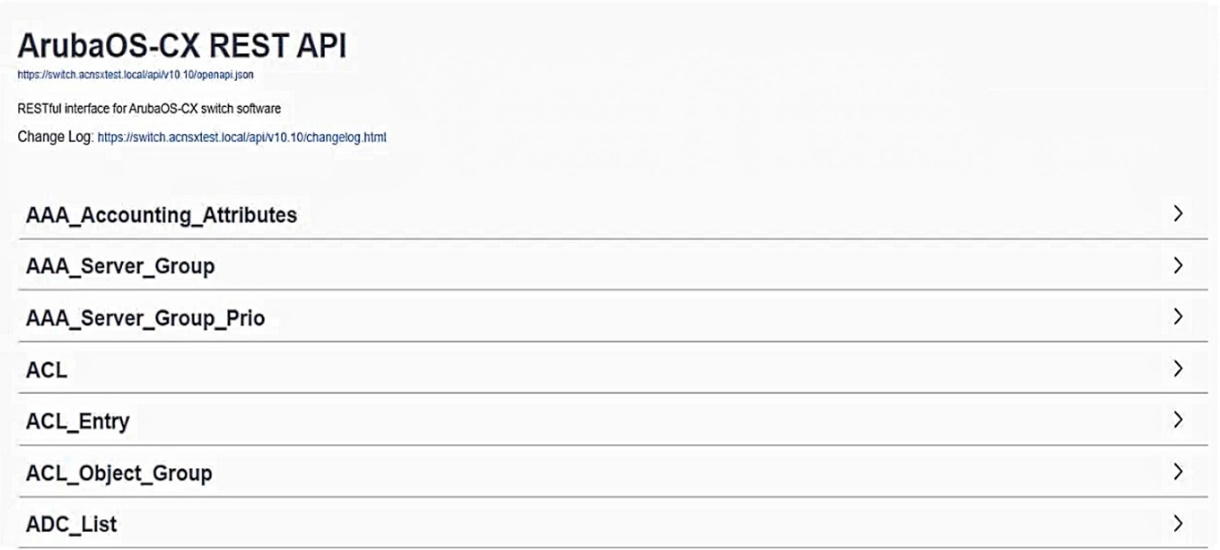
What should you do before proceeding?
Start a Discussions
A customer has an AOS 10 architecture, which includes Aruba APs. Admins have recently enabled WIDS at the high level. They also enabled alerts and email notifications for several events, as shown in the exhibit.
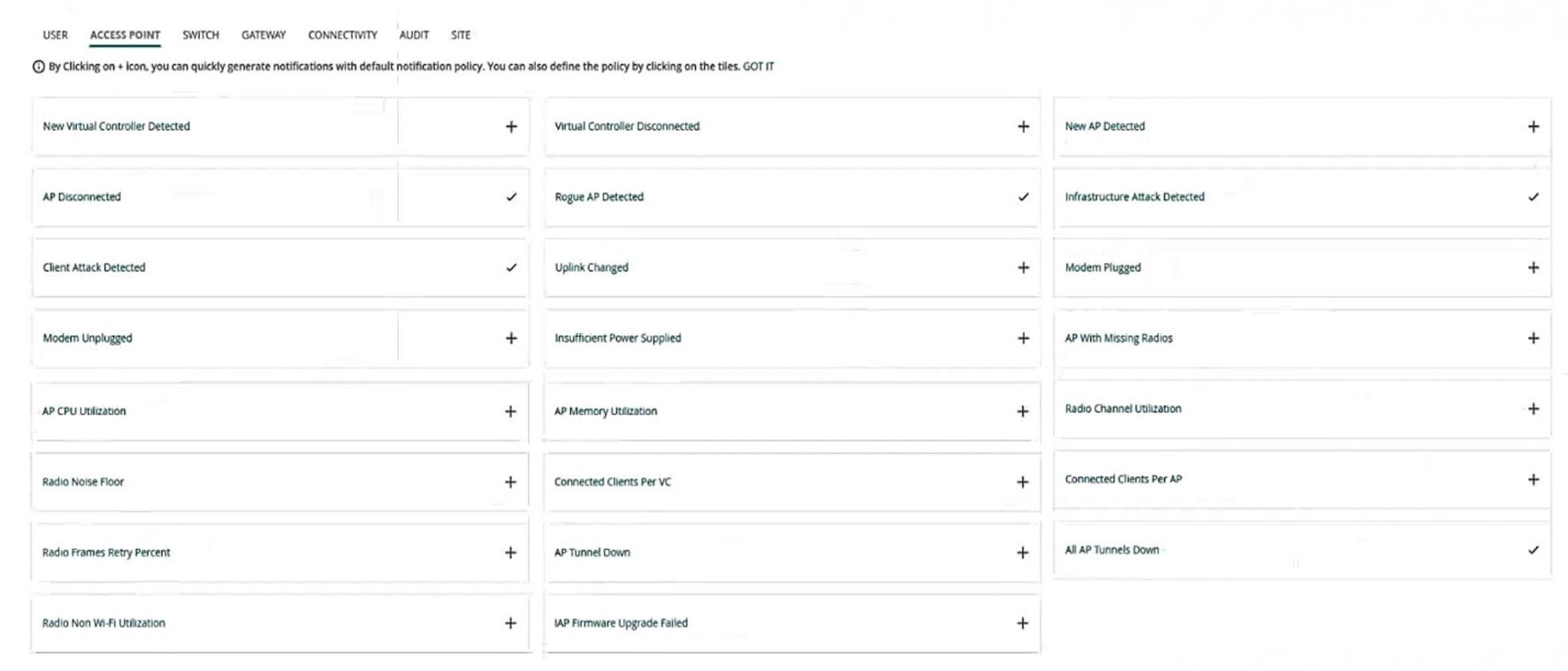
Admins are complaining that they are getting so many emails that they have to ignore them, so they are going to turn off all notifications.
What is one step you could recommend trying first?
Correct : C
Therefore, one step that could be recommended to reduce the number of email notifications is to change the WIDS level to custom, and enable only the checks most likely to indicate real threats. This way, the administrators can fine-tune the WIDS settings to suit their network environment and security needs, and avoid getting flooded with irrelevant or redundant alerts. Option C is the correct answer.
Option A is incorrect because sending the email notifications directly to a specific folder and only checking the folder once a week is not a good practice for security management. This could lead to missing or ignoring important alerts that require immediate attention or action. Moreover, this does not solve the problem of getting too many emails in the first place.
Option B is incorrect because disabling email notifications for Rogue AP, but leaving the Infrastructure Attack Detected and Client Attack Detected notifications on, is not a sufficient solution. Rogue APs are unauthorized access points that can pose a serious security risk to the network, as they can be used to intercept or steal sensitive data, launch attacks, or compromise network performance. Therefore, disabling email notifications for Rogue APs could result in missing critical alerts that need to be addressed.
Option D is incorrect because disabling just the Rogue AP and Client Attack Detected alerts, as they overlap with the Infrastructure Attack Detected alert, is not a valid assumption. The Infrastructure Attack Detected alert covers a broad range of attacks that target the network infrastructure, such as deauthentication attacks, spoofing attacks, denial-of-service attacks, etc. The Rogue AP and Client Attack Detected alerts are more specific and focus on detecting and classifying rogue devices and clients that may be involved in such attacks. Therefore, disabling these alerts could result in losing valuable information about the source and nature of the attacks.
Start a Discussions
Total 60 questions