Unlock HP Aruba Mastery: HPE7-A02 Success Awaits!
Refer to the Exhibit:
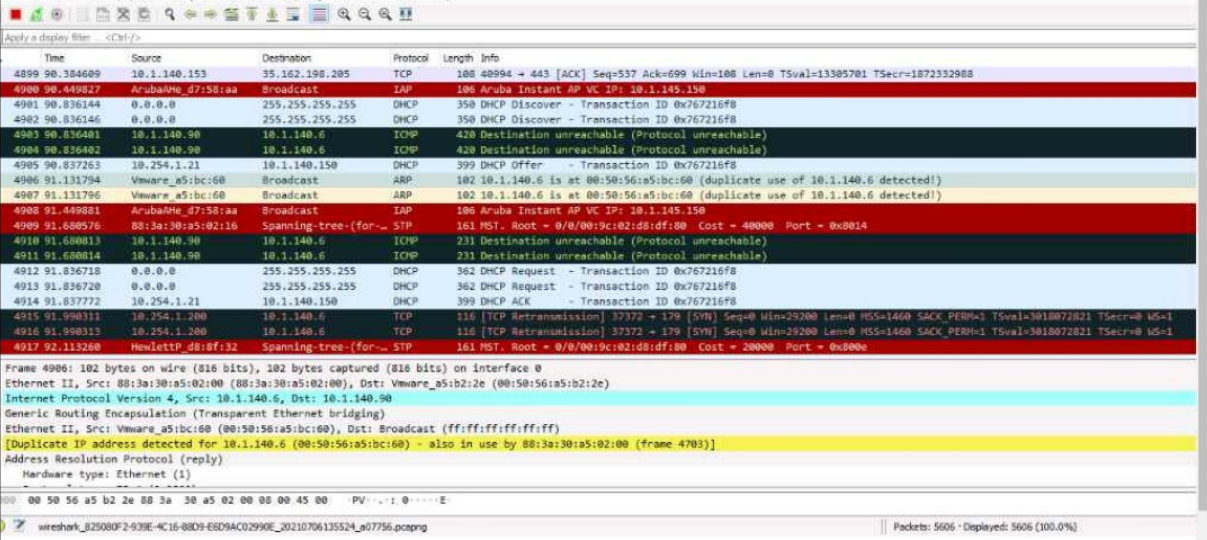
These packets have been captured from VLAN 10. which supports clients that receive their IP addresses with DHCP.
What can you interpret from the packets that you see here?
These packets have been captured from VLAN 10, which supports clients that receive their IP addresses with DHCP. What can you interpret from the packets that you see here?
Correct : A
The exhibit reveals duplicate IP addresses detected for 10.1.140.6, associated with two different MAC addresses:
88:56:56:ab:c6:89
88:13:30:a3:02:00
Key observations:
Duplicate IP Address Detection:
The message 'Duplicate IP address detected for 10.1.140.6' clearly indicates two devices claiming the same IP address.
This typically occurs when one device spoofs the MAC address of another device to intercept or disrupt traffic.
MAC Spoofing Context:
MAC spoofing is a tactic used to impersonate another device's hardware address to gain unauthorized access to a network.
By spoofing a legitimate IP-MAC pairing, an attacker can bypass security mechanisms or cause denial-of-service conditions.
Why the Other Options are Incorrect:
Option B (Mirroring Misconfigured): While mirroring misconfiguration can duplicate traffic, it does not lead to a 'duplicate IP detected' alert.
Option C (Misconfigured DHCP): Misconfigurations usually result in DHCP conflicts, but they do not typically involve two different MAC addresses for the same IP.
Option D (ARP Poisoning/MITM): ARP poisoning involves falsified ARP tables, but it does not directly trigger duplicate IP address detection. Instead, ARP packets flood the network.
Conclusion:
The evidence strongly suggests MAC spoofing, as two different MAC addresses are claiming the same IP address (10.1.140.6). This behavior is typical of attempts to gain unauthorized access or disrupt network operations.
Start a Discussions
A company is using HPE Aruba Networking Central SD-WAN Orchestrator to establish a hub-spoke VPN between branch gateways (BGWs) at 1164 site and VPNCs at multiple data centers. What is part of the configuration that admins need to complete?
Correct : C
Hub-Spoke VPN Configuration:
HPE Aruba Central SD-WAN Orchestrator enables hub-spoke topology where branch gateways (BGWs) connect to VPN concentrators (VPNCs) located at data centers.
A key step in configuring this is defining which VPNCs the BGWs will prefer for connectivity.
The DC Preference List is configured in the BGW groups to prioritize the data centers to which BGWs connect.
Option Analysis:
Option A: Incorrect. VPN pools control IP allocation, not which branches connect to VPNCs.
Option B: Incorrect. IKE policies define key exchange mechanisms but are not part of the connection preference process.
Option C: Correct. Admins configure a DC preference list in BGW groups to determine connectivity priorities with VPNCs.
Option D: Incorrect. IPsec policies define encryption parameters at a global level, but this is not specific to the hub-spoke connection configuration.
Start a Discussions
A company has HPE Aruba Networking APs running AOS-10 that connect to AOS-CX switches. The APs will:
Authenticate as 802.1X supplicants to HPE Aruba Networking ClearPass Policy Manager (CPPM)
Be assigned to the "APs" role on the switches
Have their traffic forwarded locally
What information do you need to help you determine the VLAN settings for the "APs" role?
Correct : B
Traffic Forwarding for APs:
In AOS-10, AP traffic forwarding can happen locally (bridged) or through tunnels to a gateway.
The VLAN settings on the 'APs' role depend on whether the APs bridge the SSID traffic locally or forward it through a tunnel.
Option B: Correct. You need to know whether the traffic is bridged or tunneled to determine the VLAN assignments.
Option A: Incorrect. LURs/DURs affect role assignment but not VLAN settings for traffic forwarding.
Option C: Incorrect. Establishing tunnels with gateways is relevant to centralized traffic forwarding, not VLANs for bridged traffic.
Option D: Incorrect. AP IP addressing (static or DHCP) does not impact the VLAN for forwarded SSID traffic.
Start a Discussions
A company has AOS-CX switches, which authenticate clients to HPE Aruba Networking ClearPass Policy Manager (CPPM). CPPM is set up to receive a variety of information about clients' profile and posture. New information can mean that CPPM should change a client's enforcement profile. What should you set up on the switches to help the solution function correctly?
Correct : C
Dynamic Authorization for Enforcement Profile Updates:
When CPPM receives updated client posture or profile data, it can initiate a Change of Authorization (CoA) to update enforcement profiles dynamically.
To support this:
Dynamic Authorization must be enabled on the switches.
CPPM must be configured as a dynamic authorization client to send CoA requests.
Option C: Correct. Dynamic authorization ensures that the switch can apply updated enforcement profiles based on new information from CPPM.
Option A: Incorrect. RADIUS accounting provides session updates but does not enable dynamic changes to enforcement profiles.
Option B: Incorrect. RADIUS track is for monitoring RADIUS server availability, not dynamic enforcement updates.
Option D: Incorrect. TACACS is not used for dynamic authorization; RADIUS handles this functionality.
Start a Discussions
A company already uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as the RADIUS server for authenticating wireless clients with 802.1X. Now you are setting up 802.1X on AOS-CX switches to authenticate many of those same clients on wired connections. You decide to copy CPPM's wireless 802.1X service and then edit it with a new name and enforcement policy. What else must you change for authentication to work properly?
Correct : D
802.1X Service Rules:
Service rules define the criteria for when a specific service applies (e.g., wireless vs. wired authentication).
For wired 802.1X authentication to work properly, the service rules need to differentiate between wireless and wired connections.
If you copy the wireless service, the rules likely still match wireless-specific criteria. These must be updated to include wired-specific conditions (e.g., NAS IP or port types).
Option Analysis:
Option A (Role mapping policy): Role mapping policies determine user roles based on attributes but are not critical for differentiating wired vs. wireless.
Option B (Authentication methods): Authentication methods (e.g., EAP) remain the same for both wireless and wired 802.1X.
Option C (Authentication source): Authentication sources (like AD or internal database) do not need to change.
Option D (Service rules): Correct. Updating the service rules ensures the new 802.1X service applies specifically to wired connections.
Start a Discussions
Total 130 questions