Unlock Juniper Security Mastery: Specialist JN0-335 Success Awaits
You want to set up JSA to collect network traffic flows from network devices on your network.
Which two statements are correct when performing this task? (Choose two.)
Correct : A, C
The two correct statements when performing this task are A. BGP FlowSpec is used to collect traffic flows from Junos OS devices, and C. Statistical sampling decreases event correlation accuracy. BGP FlowSpec is a Junos OS feature that allows network devices to send traffic flow information to a Juniper security device using BGP. This allows the Juniper security device to monitor and collect the traffic flows and analyze them for suspicious activity. Statistical sampling increases processor utilization by selecting only a subset of the data to be analyzed, which can help reduce the amount of data sent to the security device. However, this also decreases the accuracy of event correlation, as some events may be missed due to the sampling. Superflows reduce traffic licensing requirements by offloading the processing of certain traffic flows to the device itself, instead of having it sent to the security device.
Start a Discussions
What information does encrypted traffic insights (ETI) use to notify SRX Series devices about known malware sites?
Correct : D
Encrypted traffic insights (ETI) uses domain names to notify SRX Series devices about known malware sites. ETI is a feature of the SRX Series firewall that can detect and block malware that is hidden in encrypted traffic. It works by analyzing the domain names of the websites that the encrypted traffic is attempting to access. If the domain name matches a known malware site, ETI will send an alert to the SRX Series device, which can then take appropriate action to block the traffic. ETI is a useful tool for protecting against threats that attempt to evade detection by hiding in encrypted traffic.
Start a Discussions
Exhibit
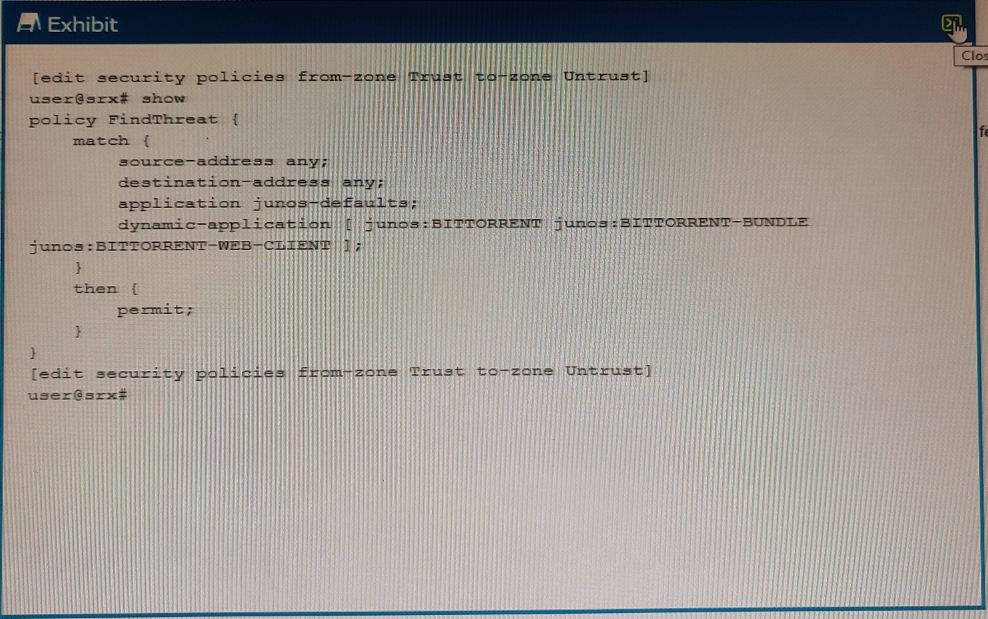
You are asked to track BitTorrent traffic on your network. You need to automatically add the workstations to the High_Risk_Workstations feed and the servers to the BitTorrent_Servers feed automatically to help mitigate future threats.
Which two commands would add this functionality to the FindThreat policy? (Choose two.)
A)
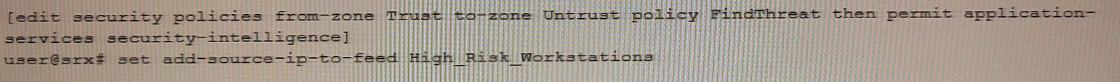
B)
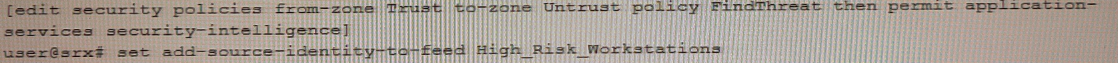
C)

D)

Correct : C
Start a Discussions
Which two types of SSL proxy are available on SRX Series devices? (Choose two.)
Correct : B, C
Based on SSL proxy is a feature that allows SRX Series devices to decrypt and inspect SSL/TLS traffic for security purposes. According to SRX Series devices support two types of SSL proxy:
Client-protection SSL proxy also known as forward proxy --- The SRX Series device resides between the internal client and outside server. It decrypts and inspects traffic from internal users to the web.
Server-protection SSL proxy also known as reverse proxy --- The SRX Series device resides between outside clients and internal servers. It decrypts and inspects traffic from web users to internal servers.
Start a Discussions
Which two statements about SRX Series device chassis clusters are correct? (Choose two.)
Correct : A, D
Two statements that are correct about SRX Series device chassis clusters are:
The chassis cluster data plane is connected with revenue ports: A chassis cluster is a high-availability feature that groups two identical SRX Series devices into a cluster that acts as a single device. The cluster has two types of links: control links and fabric links. The control links are used for exchanging heartbeat messages and configuration synchronization between the nodes. The fabric links are used for forwarding data traffic between the nodes. The fabric links are connected with revenue ports, which are regular Ethernet interfaces that can also be used for normal traffic when not in cluster mode.
The chassis cluster can contain a maximum of two devices: A chassis cluster can only consist of two nodes: node 0 and node 1. The nodes must be the same model, have the same hardware configuration, run the same software version, and have the same license keys. The nodes share a common configuration and act as backup for each other in case of failure.
Start a Discussions
Total 98 questions